Computer Networks Structure
Introduction to Backbone, Three-Tiered, Traffic Flow...
Disclaimer
This content is provided for educational and informational purposes only. The techniques and tools discussed, are intended to raise awareness about security risks and help developers and system administrators protect their systems.
We do not encourage, support, or condone any form of unauthorized access, exploitation, or malicious activity. All demonstrations were conducted in controlled environments with proper authorization.
Use this knowledge responsibly and always adhere to your local laws and ethical guidelines. Hacking should only be performed in environments where you have explicit permission.
The author assumes no responsibility for any damages or legal consequences arising from the misuse of this content. Always ensure you have proper authorization before testing or auditing any system!
Backbone
In today’s complex networks, there’s a need for a standard way to communicate clearly about what part of the network you are referring to. So networks are broken down into different parts called backbones and segments.
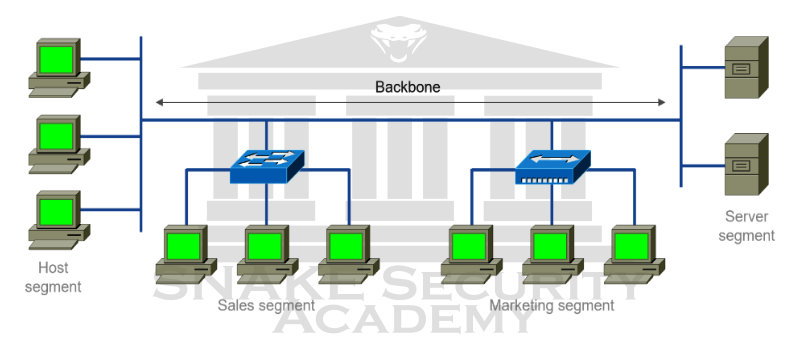
As you can see, the backbone of the network is actually a bit like the backbone of our own human body. It’s what gives the network its structure, and it’s what all the network segments and servers connect to. Since the backbone is such an important nerve center, it has to be built with some kind of really fast, robust technology - often Gigabit Ethernet or faster.
Segments
A segment is any small portion of the network that may have a connection to the backbone but is not actually part of it. The network backbone, which is the common connection point for all segments, is connected to the network workstations and servers organized into segments…
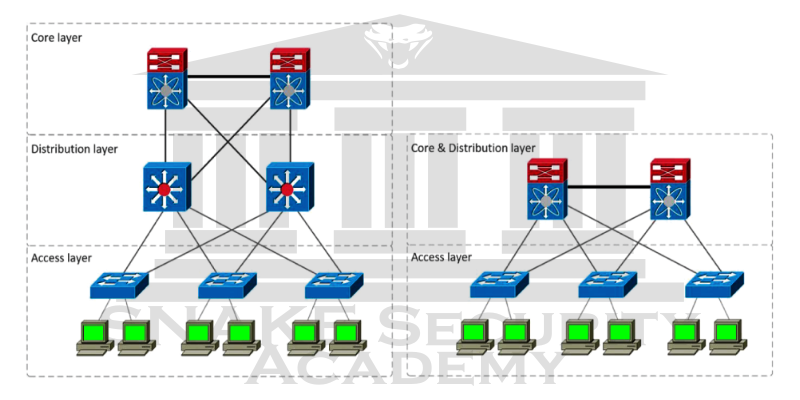
Three-Tiered Model
The Three-tiered networking model was introduced by Cisco in 1998, and it’s become the gold standard for how networks are designed. It still holds true today for any hardware vendor, even though it was introduced so long ago.

Today’s small-to-medium network designs have adopted the collapsed-core model to eliminate the cost of additional network switching.
-
Core Layer : The core layer is considered the network backbone. This is where you will find the WAN links that connect and interconnect geographic areas. It only provides routing and switching for the entire network and should be designed for high availability. The core layer should not do anything that is a source of network latency!
-
Distribution Layer : This layer is frequently referred to as a workload layer or an aggregated layer due to its ability to connect to multiple access layer switches. The distribution layer is where packet filtering, security policies, routing between VLANs, and broadcast domain definition takes place, and where the control plane resides. Think about it as distributing switching from the core to the access layer.
-
Access Layer : Often referred to as the edge switching layer, the access layer connects end user hosts. Local switching and collision domain creation is done at the access layer. It is designed for simple network access and is where Quality of Service (QoS), Power over Ethernet (PoE), and security support begins.
To reduce the cost and complexity of networks, the collapsed-core model was introduced. We can support both the core and distribution layers on the same piece of network switching equipment with today’s high-performance switching. It is just collapsed into one piece of switching equipment and still performs the same functions as the core and distribution layers.
Traffic Flow
An understanding of the flow of traffic through your networks is important. But why? Why should you have an understanding of the type and direction of traffic flowing through your network?
There are a lot of reasons, but the most important one, and the one we’re going to focus on here, is security.
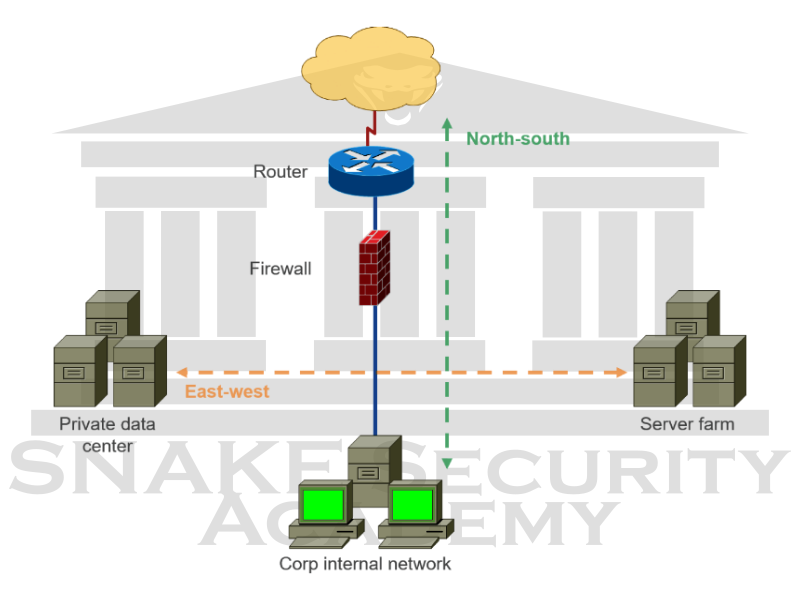
Initially, north-south traffic is going to be the most important security concern, because the data will be flowing to and from your corporate network to the outside Internet. But that doesn’t mean you shouldn’t take the security of east-west traffic seriously as well.
Let’s analyze the 2 scenarios
-
North-South : We can see the traffic we find here coming in and out of your internal network. Strong security is essential at this point. A firewall and routers allow the southbound traffic to enter. The northbound traffic is on its way from your internal network to the Internet.
-
East-West : The east-west traffic is still important to understand that there are many types of attacks, especially from the inside, that need to be taken seriously. You need to look at the lateral traffic that is going between the server farms and the data centers. There is an enormous amount of traffic there, and some examples of east-west traffic include database replication, file transfers, and interprocess communication.
